With several large data breaches taking place in Australia during 2022. Cybersecurity is certainly at the forefront of business owners’ minds. Indeed, a recent report from the Australian Cyber Security Centre ACSC reveals that 1 incident is reported every 10 minutes. That is approximately 144 cyber incidents a day, with the estimated annual losses to businesses totalling around $300 million per year.
Yet despite this very real and very present threat of cybercrime, many SMBs either lack the resources to implement comprehensive cybersecurity measures or may be unaware of how vulnerable their business is. Indeed;
“The ACSC acknowledges that Australian small to medium businesses (SMBs) operate in a different environment compared to larger enterprises, with 97% of Australian businesses having less than 20 staff.”
In short, every organisation is a potential target for cybercriminals. Luckily, practising good cyber hygiene is also something any organisation can achieve. However, there are also plenty of effective and inexpensive mitigation measures. Small businesses can implement to defend themselves against cyber incidents.
The Essential Eight from the ACSC is a great place to start when developing a cybersecurity strategy for your organisation.
It broadly breaks down into application control, patch applications, configuration Microsoft Office macro settings, user application hardening, restricting administrative privileges, patching operating systems, multi-factor authentication and regular backups.
As specialists across Business Management applications such as ERP systems, Payroll and Software Development, Alphabiz have the knowledge and expertise to assist you to protect your critical data and business infrastructure. Here are 5 ways we can help keep your organisation safe:
Backup your data and systems
Having witnessed businesses losing their data due to hard drive crashes or, as happens more frequently nowadays, being the target of a ransomware attack. Today’s backup solutions are sophisticated, offering both local and offsite in the way of data volumes, data compression, access to open files and much more.
The two most common backup methods are:
- The 3-2-1 rule – have at least three copies of your data. Two stored locally (on-site) and at least one copy off-site.
- The Grandfather-father-son (GFS) – is a standard rotation scheme for backing up media. Three backup cycles are implemented, for instance daily, weekly and monthly.
Always find out what backup method your IT partner is using. Run tests to ensure deleted or corrupted files are recoverable. Nevertheless, you should still check what data backup and recovery services are available as part of your cloud subscription and/or Service Level Agreement.
Enforce a complex secure password
All too often we come across insecure user login credentials, using something as basic as the user’s first name/last name and letting the user choose whatever password they please. Enforce a complex secure password policy along with multi-factor authentication (MFA) at a minimum.
Many systems already do this, for example, MYOB Advanced prompts users to turn on MFA. Along with educating employees on the importance of secure protect both their own and the company’s data. System administrators should also ensure staff have secure sign-on and strong passwords enabled as part of the onboarding process.
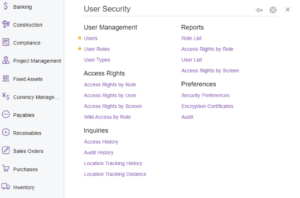
Restrict user roles control
Restricting users with roles that control which departments, modules, screens and functions they can access, edit and delete adds another layer of security.
Not only will it help protect organisational data from malicious breaches, but it could also potentially limit the extent to which malicious programmes can propagate and cause damage.
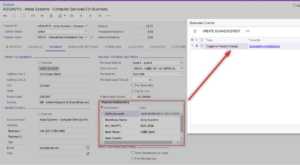
Set up notification events
This will help you protect against email scammers spoofing your suppliers. By setting up notification events to alert management whenever a supplier has changed their bank details in the system.
Also, try to avoid processing bank payments manually and use the ABA file generated from the system. Look out for an upcoming blog from Alphabiz about how you can use your ERP to mitigate employee fraud.
Be vigilant to suspicious links on email
Phishing emails aren’t just a nuisance—they’re a serious threat to your business.
The email may contain a link or would request the recipient’s essential information. Once done, malicious software will be downloaded to their computer which puts their system data at risk.
A robust company policy that prohibits sharing usernames and passwords over email can help protect your organisation against this kind of malicious activity.

Alphabiz Solutions can help secure your systems.
Our ERP experts can assist you in developing and implementing best practices for cybersecurity. Book a consultation today!